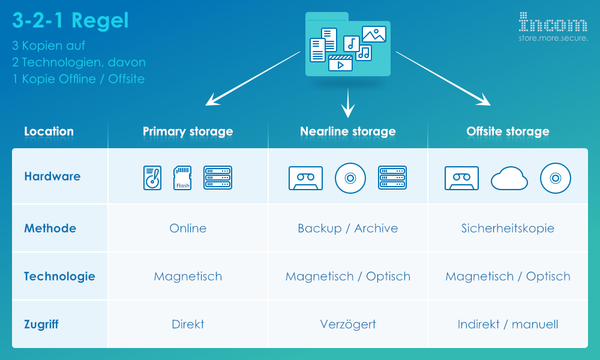
The golden rule for secure data storage, the so-called 3-2-1 principle, was coined by the American photographer Peter Krogh, who, after a data loss, propagated the solution approach that data is stored in 3 copies on 2 different storage technologies and of which one version should be kept off-site in order to be protected as much as possible from any data loss.
Normally, the productive data of a company is stored on a server hard disk, which in the best case promises minimal security when used in a raid network. Depending on the raid level, individual hard disks can fail without data being lost.
If data is lost or damaged by viruses or similar, an external backup helps to restore the information quickly. Depending on the amount of data, a backup can also reach its limits, because the time needed for a backup is not infinite. If you remove the data that is no longer changed but still needs to be present and add it to a proper long-term archive in a secondary storage such as the StorEasy WormAppliance or a HIT Netzon Library, this not only creates an enormous amount of free space in the backup window, but also relieves the usually expensive primary storage.
This can also be organized by a storage management software like PoINT Storage Manager, which is able to organize the data between storage systems and locations automatically.